Attack Flow Gallery
Explore interactive attack flow visualizations powered by FlowViz. Analyze real-world cyber attacks with MITRE ATT&CK mapping and discover threat intelligence patterns.

Operation FrostBeacon: Multi-Cluster Cobalt Strike Campaign Targets Russia
# Incident Report: Operation FrostBeacon Cobalt Strike Campaign ## Executive Summary Operation FrostBeacon is a financially motivated, multi-cluster malware campaign utilizing sophisticated phishing techniques to deploy Cobalt Strike beacons targeting B2B enterprises in the Russian Federation. The primary attack vectors involve weaponized archive delivery containing malicious LNK files or the chaining of legacy Microsoft Office vulnerabilities (CVE-2017-0199 and CVE-2017-11882) to achieve remote HTA execution, ultimately deploying an obfuscated PowerShell payload. The campaign demonstrates high operational security, leveraging Russian-controlled infrastructure for C2 communications. ## Incident Details - **Discovery Date:** Implied to be ongoing, with first-seen telemetry on 2025-11-06 00:08:46 UTC for the LNK cluster. - **Incident Date:** Ongoing throughout late 2025 (based on timestamps). - **Affected Organization:** Multiple B2B enterprises. - **Sector:** Logistics, industrial production, construction, and technical supply. - **Geography:** Russian Federation. ## Timeline of Events ### Initial Access - **Date/Time:** Ongoing (First observed 2025-11-06 UTC). - **Vector:** Phishing Emails delivering weaponized ZIP/RAR archives. - **Details:** * **LNK Cluster:** Phishing emails contained archives (e.g., `рекламация.zip`) holding a decoy Excel document and a malicious LNK file (`рекламация.pdf.lnk`). * **CVE Cluster:** Phishing emails exploited template injection vulnerabilities, specifically chaining **CVE-2017-0199** and **CVE-2017-11882**. ### Lateral Movement - **Details:** Not explicitly detailed beyond initial payload execution, but the use of Cobalt Strike implies subsequent capabilities for host discovery and lateral movement via C2 communication. ### Data Exfiltration/Impact - **Details:** The goal is financially motivated targeting departments handling payments, contracts, and legal risk. The final payload is a Cobalt Strike beacon, suggesting full remote control and data exfiltration capabilities, though specific data impacts are not detailed. ### Detection & Response - **Details:** Seqrite Labs identified and analyzed the campaign. The report details the analysis of the malware workflow, infrastructure hunting, and payload dissection. No specific containment or eradication actions taken by the victim organizations are detailed, only the analysis performed by Seqrite. ## Attack Methodology - **Initial Access:** Spearphishing Attachment (T1566.001), User Execution: Malicious File (T1204.002), Template Injection Execution (T1221). - **Persistence:** Implied via Cobalt Strike deployment, though specific persistence mechanisms are not detailed in the summary. - **Privilege Escalation:** Not explicitly detailed, but necessary to fully deploy the next stage. - **Defense Evasion:** Obfuscated commands (`powershell -WindowStyle Hidden`), Obfuscated/Encoded Files (PowerShell shellcode decryption in memory), Deobfuscation triggered by `mshta.exe` execution. - **Credential Access:** Not explicitly detailed, but standard for Cobalt Strike post-exploitation. - **Discovery:** System Information Discovery (T1082), System Network Configuration Discovery (T1016). - **Lateral Movement:** Standard Cobalt Strike functionality (implied). - **Collection:** Not explicitly detailed. - **Exfiltration:** Through command and control channels established by Cobalt Strike (T1071.001). - **Impact:** Installation of C2 implant (Cobalt Strike beacon). ## Impact Assessment - **Financial:** Motivated by financial gain, targeting finance/payment departments. - **Data Breach:** High potential for sensitive financial and legal data compromise due to financial motivation and C2 deployment. - **Operational:** Disruption due to system compromise and ongoing attacker control. - **Reputational:** High risk given the nature of targeting Russian B2B enterprises. ## Indicators of Compromise - **Network Indicators (Defanged):** * **Domains:** `update.ecols[.]ru`, `incident.zilab[.]ru`, `mcnn[.]ru`, `order.edrennikov[.]ru`, `cba.abc92[.]ru`, `forensics.jwork[.]ru`, `hostbynet[.]ru`, `moscable77[.]ru`, `gk-stst[.]ru`, `aquacomplect[.]ru`, `ezstat[.]ru`, `ekostroy33[.]ru`, `valisi[.]ru`, `bsprofi[.]ru`, `iplis[.]ru`, `zetag[.]ru`, `lieri[.]ru`, `dosingpumps[.]ru`, `esetnod64[.]ru`, `yadro[.]ru`, `iplogger[.]ru`, `krona77[.]ru`, `bti25[.]ru`. * **Proxy IPs:** `45.147.14.106:62900`, `45.145.91.164:64830`. - **File Indicators:** * **MD5 (LNK File):** `16ae36df5bee92d8c4cae8e17583a2c9` * **MD5 (Archive):** `7096141a5b480e793e9a890b84ebaee2` - **Behavioral Indicators:** Remote HTA execution triggered by PowerShell launched from hidden window mode; utilization of default Cobalt Strike malleable profile. ## Response Actions - **Containment Measures:** Not explicitly detailed in the summary, assumed to be necessary based on IOCs. - **Eradication Steps:** Not explicitly detailed. - **Recovery Actions:** Not explicitly detailed. ## Lessons Learned - Attackers continue to exploit legacy, unpatched vulnerabilities (CVE-2017-0199/11882) as a viable infection vector against less mature environments. - Social engineering is highly effective when native language lures (Russian terms like "сводная" or "рекламация") are used, focusing on high-value workflows (finance, legal). - The use of multi-layered infection chains, culminating in memory-only execution via PowerShell, significantly complicates detection. - Attackers utilize infrastructure disguised as legitimate services (e.g., IP logging services, standard Javascript names) for C2 hosting. ## Recommendations - **Patch Management:** Immediately prioritize patching legacy vulnerabilities, especially those related to Microsoft Office document parsing and template injection. - **Email Security:** Implement strict email filtering rules and advanced sandboxing to block or detonate archives containing LNK files or known malicious macros/templates. - **User Training:** Conduct targeted security awareness training focusing on ISO-9001/financial correspondence lures and the dangers of opening unexpected attachments, even if they appear to be PDFs or Excel files disguised by double extensions. - **Endpoint Detection & Response (EDR):** Configure EDR solutions to aggressively monitor for suspicious parent/child processes, specifically `cmd.exe` launching `powershell.exe` with hidden windows, and the subsequent execution of `mshta.exe` via command line arguments.
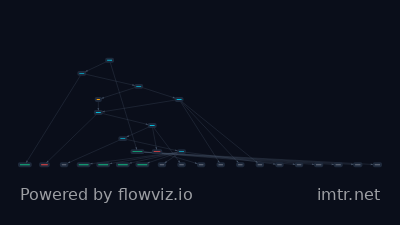
Inside the CopyCop Playbook: How to Fight Back in the Age of Synthetic Media
# Threat Actor: CopyCop (Storm-1516) ## Attribution & Identity **Attribution:** Russian influence network. **Aliases and Known Associations:** Known as **Storm-1516**. The operation is detailed in an Insikt Group report. ## Activity Summary CopyCop is engaged in scaling AI-driven influence operations globally, deploying over 300 inauthentic media websites since early 2025. These sites are designed to erode public trust and support for Ukraine by advancing Russia’s geopolitical objectives and deepening political fragmentation in supporting Western nations. Recent activities include: * Forging “leaked documents” alleging misuse of Western aid by Ukrainian officials. * Creating deepfake videos falsely accusing Armenian officials and publishing fabricated stories about French leaders being corrupt. * Impersonating French and Moldovan media outlets to push corruption and election interference narratives. * Promoting pro-independence sentiment and amplifying domestic polarization in Canada’s Alberta province via inauthentic websites. ## Tactics, Techniques & Procedures - **AI-Generated Content Scale:** Mass-producing fabricated news stories, deepfakes, and fake fact-checking sites using self-hosted Large Language Models (LLMs), specifically uncensored open-source versions. - **Content Generation TTPs:** Generating articles that weave together real and fabricated details, complete with bylines, using LLMs fine-tuned on Russian state media sources. Telltale AI artifacts include phrases like: "Please note that this rewrite aims to provide a clear and concise summary of the original text while maintaining key details." - **Infrastructure Cloning:** Operating a vast web of cloned domains and mirrored subdomains imitating legitimate local media outlets, political parties, or fact-checking organizations. - **Distributed Infrastructure:** Building systems designed to withstand disruption, with mirrored copies appearing elsewhere when a domain is taken down, often hosted on similar IP ranges. - **Narrative Amplification:** Amplifying narratives through a secondary ecosystem including Telegram channels, YouTube accounts, and pro-Russian influencers like InfoDefense and Portal Kombat. - **Information Poisoning:** Deliberately flooding the internet with synthetic "news" to contaminate data sources (LLMs, search engines, AI assistants) relied upon for generating information. ## Targeting - **Sectors:** General public, political institutions, media organizations, and organizations involved in providing aid/funding to Ukraine (implied by forged documents). - **Geography:** Global reach, with specific deployment across North America and Europe, including Armenia, Moldova, and parts of Africa. - **Victims:** Western leaders, institutions, media, Ukrainian officials, Armenian officials, and French leaders. ## Tools & Infrastructure - **Malware Families Used:** Not explicitly detailed, but relies heavily on **self-hosted, uncensored Large Language Models (LLMs)**. - **Infrastructure (C2, domains, IPs - defang URLs):** Over 300 inauthentic websites disguised as local news outlets, political parties, and fact-checking organizations. Infrastructure is distributed and uses mirrored subdomains hosted across known IP ranges to survive takedowns. ## Implications CopyCop represents a significant evolution in influence operations by fully weaponizing generative AI to produce high-volume, personalized disinformation at scale. This threatens the integrity of the global information supply chain by poisoning algorithmic data sources relied upon by modern AI tools, potentially undermining democratic institutions and sustained international support efforts for Ukraine. ## Mitigations - **Domain Monitoring:** Governments should monitor domain registrations and hosting infrastructure to detect clusters of inauthentic media sites. - **Intelligence Integration:** Integrate threat intelligence feeds into election-security and information-integrity programs. - **Content Verification:** Newsrooms must strengthen verification workflows to detect AI-generated text, deepfakes, and synthetic imagery. - **Look-Alike Detection:** Use threat intelligence to identify look-alike domains mimicking legitimate outlets. - **Staff Training:** Train editorial staff on recognizing LLM-generated content telltale signs and suspicious bylines. - **Brand Monitoring:** Enterprises should deploy brand-intelligence monitoring to uncover impersonation campaigns. - **Incident Response:** Develop incident-response plans specifically tailored for influence operations. - **Proactive Communication:** Communicate proactively and transparently when false narratives arise. - **General User Practice:** Practice verification before amplification (questioning sources before sharing).
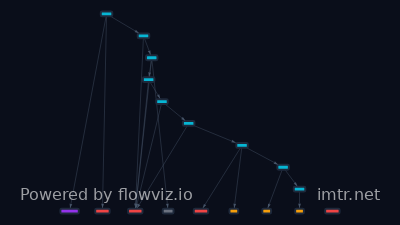
ToddyCat’s New Hacking Tools Steal Outlook Emails and Microsoft 365 Access Tokens
# Threat Actor: ToddyCat ## Attribution & Identity - **Identification:** Threat actor known as ToddyCat. - **Aliases/Associations:** None explicitly mentioned beyond the primary name. Assessed to be active since 2020. ## Activity Summary ToddyCat has been observed deploying new methods to access and steal corporate email data from targeted organizations. Recent activities show a focus on obtaining access tokens for the OAuth 2.0 protocol and exfiltrating data from Microsoft Outlook. The actor constantly develops new techniques to hide activity and gain continued access to corporate correspondence. ## Tactics, Techniques & Procedures - **New Access/Token Acquisition (OAuth 2.0):** Obtaining tokens for the OAuth 2.0 authorization protocol using the user's browser, allowing post-compromise access outside the network perimeter. - **Email Data Access (Local Outlook):** Bypassing restrictions to access corporate emails stored in local Microsoft Outlook OST files while the application is running, by copying the files sector-by-sector. - **Credential/Cookie Theft (Browser):** Historical/ongoing use of tools to steal cookies and credentials from web browsers (Google Chrome, Microsoft Edge, Mozilla Firefox). - **Persistence/Delivery:** Use of scheduled tasks to execute threat payloads (e.g., PowerShell variants of TomBerBil). - **Data Exfiltration Preparation (DPAPI):** Copying files containing encryption keys used by Windows Data Protection API (DPAPI) to enable local decryption of stolen browser data using the user's SID and password. - **Memory Scraping/Dumping:** Attempting to obtain JSON web tokens (JWTs) directly from memory when targets use Microsoft 365, sometimes requiring the use of Sysinternals **ProcDump** to dump the **Outlook.exe** process memory after security software blocked initial attempts with **SharpTokenFinder**. - **Exploitation (Historical):** Exploitation of a security flaw in ESET Command Line Scanner (CVE-2024-11859) to deliver malware. ## Targeting - **Sectors:** Corporate organizations (general targeting mentioned). - **Geography:** Europe and Asia. - **Victims:** Not explicitly named in the provided text. ## Tools & Infrastructure - **Custom Tools:** - **TCSectorCopy:** C++ tool used to copy OST files sector-by-sector by reading the disk as a read-only device. - **TomBerBil:** Malware previously seen in C++ and C# versions. A newer PowerShell variant targets data from Mozilla Firefox, runs on domain controllers, and searches remote hosts over SMB for browser files. - **TCESB:** Previously undocumented malware delivered via CVE-2024-11859 exploitation. - **Third-Party/Open-Source Tools Used:** - **SharpTokenFinder:** C# tool used to enumerate M365 applications for plaintext authentication tokens. - **ProcDump:** Used to dump the Outlook process memory when direct access was blocked. - **XstReader:** Open-source viewer used to extract contents from copied OST files. - **Infrastructure:** Not explicitly detailed for current operations, but techniques show reliance on domain controllers and SMB for internal movement. ## Implications ToddyCat demonstrates a highly adaptive approach focused directly on harvesting long-lived session credentials (OAuth tokens) or critical offline email stores (OST files). Their ability to use DPAPI keys alongside stolen credentials grants them comprehensive offline decryption capabilities for sensitive communications, bypassing perimeter security once initial access is established. ## Mitigations - Implement controls to monitor or restrict the suspicious reading of local Outlook OST files, especially via non-standard processes or direct disk access utilities (like sector copy tools). - Harden endpoint security to prevent low-level memory manipulation tools like ProcDump from targeting critical processes such as Outlook.exe. - Review M365/OAuth configuration for excessive long-lived token permissions. - Strictly control execution of PowerShell commands via scheduled tasks, especially those involving SMB connections to enumerate and copy files from domain controllers or other sensitive endpoints.

Beyond the Watering Hole: APT24's Pivot to Multi-Vector Attacks
# Threat Actor: APT24 ## Attribution & Identity * **Identification:** People's Republic of China (PRC)-nexus threat actor. * **Known Aliases:** APT24. ## Activity Summary APT24 is engaged in a long-running (spanning three years) and adaptive cyber espionage campaign. Historically, the group relied on broad **strategic web compromises** to inject malicious content onto legitimate websites. Recently, APT24 has pivoted to more sophisticated vectors, primarily targeting organizations in Taiwan. This pivot includes: 1. Repeated use of **supply chain attacks** via the compromise of a regional digital marketing firm in Taiwan, impacting over 1,000 domains, starting around July 2024. 2. Execution of **targeted spear phishing campaigns**, often abusing legitimate cloud storage platforms (Google Drive, OneDrive) for malware distribution. ## Tactics, Techniques & Procedures * **First-Stage Downloader:** Deploys **BADAUDIO**, a highly obfuscated, custom C++ first-stage downloader. * **Execution & Persistence:** Manifests as a malicious Dynamic Link Library (DLL) using **DLL Search Order Hijacking** (MITRE ATT&CK T1574.001). Recent variants use encrypted archives containing the BADAUDIO DLL alongside VBS, BAT, and LNK files to automate placement, establish persistence via legitimate executable startup entries, and trigger DLL sideloading. * **Obfuscation:** Utilizes **control flow flattening** to dismantle program logic, significantly impeding reverse engineering. * **Reconnaissance & Beaconing:** Collects basic system information (hostname, username, architecture), hashes it, and embeds it within a **cookie parameter** of an HTTP GET request to fetch the payload. * **Delivery via Web Compromise (Initial):** Injected malicious JavaScript on compromised websites, initially filtering for Windows systems and using **FingerprintJS** for browser fingerprinting (x64hash128 MurmurHash3) to validate targets before presenting a fake update pop-up to trick users into downloading BADAUDIO. * **Delivery via Supply Chain (Escalation):** Injected malicious script into a widely used JavaScript library provided by the marketing firm, sometimes leveraging a **typosquatting domain** impersonating a legitimate CDN (MITRE ATT&CK T1195.001). Later refinement involved concealing obfuscated scripts within maliciously modified **JSON files**. * **Data Exfiltration:** Conducts POST requests transmitting **Base64-encoded reconnaissance data** (host, useragent, fingerprint, etc.) to attacker endpoints (MITRE ATT&CK T1041). * **Social Engineering:** Uses lures (e.g., fake animal rescue emails) and tracks opens using **pixel tracking links** to confirm target interest. ## Targeting * **Sectors:** Broad array of subjects in earlier strategic web compromises (regional industrial concerns, recreational goods); specialized targeting post-pivot. * **Geography:** Recently pivoted to target organizations specifically in **Taiwan**. * **Victims:** A **regional digital marketing firm in Taiwan** was repeatedly compromised for supply chain exploitation. ## Tools & Infrastructure * **Malware Families:** * **BADAUDIO:** Custom C++ first-stage downloader, uses hard-coded AES key for payload decryption. * **Cobalt Strike Beacon:** Confirmed as a potential second-stage payload. * **Infrastructure (C2/Domains):** * C2 examples: clients[.]brendns[.]workers[.]dev, www[.]cundis[.]com, wispy[.]geneva[.]workers[.]dev, www[.]twisinbeth[.]com, tradostw[.]com, jarzoda[.]net, trcloudflare[.]com, roller[.]johallow[.]workers[.]dev * Strategic Web Compromise Stage 2 domains (examples): www[.]availableextens[.]com, www[.]twisinbeth[.]com, www[.]decathlonm[.]com, www[.]gerikinage[.]com, www[.]p9-car[.]com, www[.]growhth[.]com, www[.]brighyt[.]com, taiwantradoshows[.]com, jsdelivrs[.]com * **Distinctive Artifact:** A Cobalt Strike Beacon watermark hash observed: `BeudtKgqnlm0Ruvf+VYxuw==` ## Implications APT24 demonstrates persistent and sophisticated operational capabilities, adhering to the broader trend of PRC-nexus actors employing stealthy tactics. Their evolution from broad web compromises to targeted supply chain attacks showcases an adaptive approach aimed at gaining deep, persistent access for cyber espionage objectives. ## Mitigations * Implement strong detection logic for BADAUDIO-related indicators (e.g., YARA rules targeting control flow flattening, specific strings like "SystemFunction036"). * Monitor for DLL Search Order Hijacking execution patterns. * Review configurations of third-party JavaScript libraries, especially those loaded from CDNs, for malicious modifications (supply chain security). * Increase scrutiny of network traffic for malware beaconing that relies on encoded host information embedded within HTTP cookie headers. * Review and secure cloud storage usage (Google Drive, OneDrive) against archive distribution for initial access.
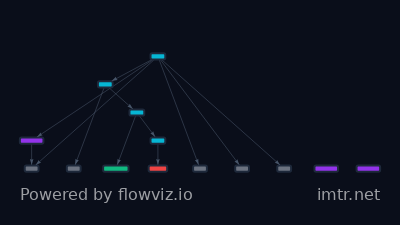
Logitech confirms data breach after Clop extortion attack
# Incident Report: Logitech Data Breach via Oracle E-Business Suite Zero-Day Exploitation ## Executive Summary Logitech confirmed a data breach resulting from a cyberattack attributed to the Clop extortion gang, who exploited a third-party zero-day vulnerability affecting their Oracle E-Business Suite environment, likely in July 2025. The incident resulted in the exfiltration of limited employee, consumer, customer, and supplier data. Logitech promptly investigated, patched the vulnerability, and affirmed that core business operations and sensitive identification/payment data were not compromised. ## Incident Details - **Discovery Date:** Prior to November 14, 2025 (Date of SEC filing/public confirmation) - **Incident Date:** Likely occurred in July 2025 (Date of Clop's associated campaign activity) - **Affected Organization:** Logitech International S.A. - **Sector:** Hardware Accessory/Electronics Manufacturing - **Geography:** Global (Swiss multinational headquarters; US SEC filing) ## Timeline of Events ### Initial Access - **Date/Time:** Prior to or during July 2025 (Coinciding with Clop's known Oracle E-Business Suite campaign). - **Vector:** Exploitation of a third-party zero-day vulnerability affecting Oracle E-Business Suite (likely CVE-2025-61882). - **Details:** Attackers leveraged the unpatched flaw in the critical business application to gain initial access. ### Lateral Movement - **Details:** Not explicitly detailed, but sufficient access was gained to conduct large-scale data exfiltration (1.8 TB allegedly stolen). ### Data Exfiltration/Impact - **Date/Time:** Data theft confirmed to have occurred prior to Clop’s public leak last week (prior to Nov 14, 2025). - **Details:** Approximately 1.8 TB of data was exfiltrated. Stolen data likely includes limited information about employees, consumers, customers, and suppliers. Sensitive PII (National ID numbers, credit card data) was not stored on the breached systems. ### Detection & Response - **How it was discovered:** The incident was initially revealed when the Clop gang added Logitech to their data-leak extortion site. - **Response actions taken:** Logitech promptly initiated an investigation utilizing external cybersecurity firms, confirmed the breach via an SEC Form 8-K, and ensured the implicated third-party zero-day vulnerability was patched as soon as a fix became available. ## Attack Methodology - **Initial Access:** Exploitation of a zero-day vulnerability in Oracle E-Business Suite (Third-Party software). - **Persistence:** Not detailed. - **Privilege Escalation:** Not detailed. - **Defense Evasion:** Not detailed in the context of this report, but typical of Clop's reliance on zero-days to bypass existing controls. - **Credential Access:** Not detailed. - **Discovery:** Not detailed. - **Lateral Movement:** Not detailed. - **Collection:** Targeting and gathering data within the compromised Oracle E-Business Suite environment. - **Exfiltration:** Stealing data to their infrastructure, later demonstrated by Clop’s public data leak. - **Impact:** Data theft and extortion attempt. ## Impact Assessment - **Financial:** Unknown costs associated with investigation and remediation, plus potential ransom payment consideration (if applicable). - **Data Breach:** Exfiltration of approximately 1.8 TB of potentially sensitive business/personal data pertaining to employees, consumers, customers, and suppliers. No sensitive payment/national ID information was reportedly stolen. - **Operational:** Logitech explicitly stated the incident did **not** impact Logitech's products, business operations, or manufacturing. - **Reputational:** Negative public disclosure via SEC filing following public extortion attempt by Clop. ## Indicators of Compromise - **Network indicators:** Log/traffic related to the exploitation of the specific Oracle E-Business Suite zero-day (Defanged Placeholder: `[Oracle_EBS_Exploit_Traffic]`). - **File indicators:** Not provided. - **Behavioral indicators:** Large-scale data staging and exfiltration activity linked to the Oracle E-Business Suite infrastructure. ## Response Actions - **Containment measures:** Prompt investigation with external cybersecurity firms; patching of the exploited zero-day vulnerability. - **Eradication steps:** Unknown, subsequent to patching. - **Recovery actions:** None explicitly detailed regarding operational recovery, as business operations were not impacted. ## Lessons Learned - Reliance on third-party software, especially critical business applications like Oracle E-Business Suite, represents a significant supply chain risk if zero-day vulnerabilities are exploited. - The ability of known threat actors like Clop to weaponize freshly disclosed vulnerabilities rapidly is a persistent threat recognized across the industry. ## Recommendations - Implement robust vulnerability management processes, prioritizing patching for critical third-party applications, especially those internet-facing or handling sensitive data. - Review and enhance segmentation around critical business systems (like Oracle EBS) to limit data access and prevent large-scale exfiltration even upon successful initial compromise. - Proactively monitor for indicators related to known campaigns by groups like Clop targeting specific software platforms.
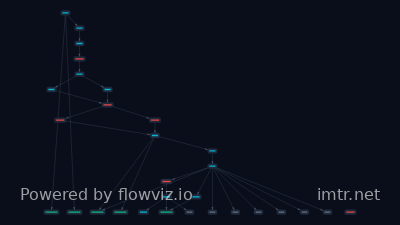
Nitrogen ransomware: From staged loader to full-scale extortion
# Threat Actor: Nitrogen Group ## Attribution & Identity * **Identification:** A sophisticated and financially motivated threat group. * **Known Aliases and Associated Groups:** No confirmed aliases are well-documented. Researchers suspect the current group may include former Blackcat operators. * **Location/Lineage:** Location and member identities are not well documented publicly. Open-source reporting links activity to the broader Eastern-European area, but this is not confirmed. C2 infrastructure has been noted in Bulgaria and the Netherlands. ## Activity Summary * **Origin:** First observed as a malware developer and operator in 2023. * **Evolution:** Has transformed into a full end-to-end, double extortion ransomware operation. * **Extortion Method:** Employs double extortion, relying on data exfiltration and system encryption. * **Leak Site:** Operates a leak site known as 'NitroBlog', which features a minimalist logo, a 'contact us' link, and a list of victims. * **Ransom Note:** Standard ransom note style, providing instructions on payment and victim deliverables. ## Tactics, Techniques & Procedures * **Initial Access:** Aggressive use of **malvertising (poisoned ads)** via platforms like Google and Bing, leading victims to trojanized installers for legitimate applications (e.g., WinSCP, Advanced IP Scanner). This technique is specifically aimed at IT professionals and other technical users. * **Ransomware Tactics:** Operates as a full ransomware operation (potentially RaaS, though unconfirmed). * **Stealth/Evasion:** Uses other cloaking techniques to remove forensic artifacts. * **Post-Infection (Implied/Suspected):** The article suggests they leverage tools traditionally associated with other operations, such as Sliver and potentially BlackCat ransomware, indicating a multi-stage or tiered deployment approach. * *Note: Specific TTPs derived from associated tool usage include:* Deployment of Sliver (Implied Initial Access/C2) and BlackCat (Implied Final Payload/Ransomware). ## Targeting * **Sectors:** Finance, manufacturing, professional services, and regional businesses. * **Geography:** Companies across the US, UK, Canada, and various international victims. * **Victims:** Companies of all sizes. ## Tools & Infrastructure * **Malware Families Used:** Associated with staging loaders; post-infection activity has been linked to deployment of **Sliver** and **BlackCat** ransomware. * **Infrastructure:** * **Leak Site:** 'NitroBlog' * **C2 Locations (Observed):** Bulgaria, Netherlands (Note: These are C2 server locations, not necessarily the actor's physical location). ## Implications The Nitrogen group represents a persistent and evolving threat due to its mastery of malvertising for initial access, sophisticated stealth techniques, and its rapid scaling into a comprehensive double extortion operation since its 2023 emergence. The minimalist branding may suggest a focus on quiet operations or preparation for future rebranding/exit strategies. ## Mitigations * **Focus on Initial Access:** Implement strong security policies around clicking external advertisements, especially those offering software downloads. Verify the source of all application installers. * **Content Filtering:** Enhance web filtering to block suspicious advertising networks or domains associated with malvertising campaigns. * **Endpoint Detection and Response (EDR):** Maintain robust EDR solutions capable of detecting post-exploitation activity associated with tools like Sliver and known ransomware payloads. * **Forensics Preparation:** Ensure logging and monitoring are configured to detect the evasion techniques used to remove forensic artifacts.

ThreatsDay Bulletin: AI Tools in Malware, Botnets, GDI Flaws, Election Attacks & More
As an Incident Response Analyst, I must first clarify that the provided text is a **compilation of disparate security news items** from a "ThreatsDay Bulletin," not a detailed report on a single, specific security incident with an established timeline. Therefore, the following summary will focus on structuring the incidents *mentioned* within the bulletin, particularly the cybercrime prosecution, as it offers the most concrete details regarding victims and attackers, while treating the GDI vulnerability discovery as a separate event. # Incident Report: Cybercrime Syndicate Prosecution & Windows GDI Flaw Discovery ## Executive Summary This report summarizes two significant security findings from the provided bulletin: the sentencing of three Chinese nationals in Singapore for a large-scale cybercrime operation targeting gambling sites, and the disclosure of multiple critical, patched GDI vulnerabilities in the Windows operating system. The cybercrime syndicate impacted overseas gambling organizations by stealing PII and possessing state-level data, while the GDI flaws permitted RCE and information disclosure via specially crafted graphic files. ## Incident Details - **Discovery Date:** May, July, and August 2025 (for GDI patches); September 2024 (for syndicate arrests). - **Incident Date:** Ongoing activity over an unknown period leading up to September 2024/November 2025 sentencing. - **Affected Organization:** Overseas gambling websites/companies; Various organizations running vulnerable Windows systems. - **Sector:** Gambling/Online Entertainment; Software Vendor (Microsoft). - **Geography:** Singapore (Prosecution); Global (Windows Vulnerabilities). ## Timeline of Events ### Initial Access (Syndicate) - **Date/Time:** Unknown, prior to September 2024. - **Vector:** System vulnerability exploitation (implied through "probe sites for system vulnerabilities"). - **Details:** Attackers targeted overseas gambling websites to gain unauthorized access for cheating purposes and data theft. ### Lateral Movement (Syndicate) - **Details:** Attackers used **PlugX** and **hundreds of different Remote Access Trojans (RATs)** to facilitate cyber attacks and maintain access. ### Data Exfiltration/Impact (Syndicate) - **Details:** Exfiltration of databases containing Personally Identifiable Information (PII) for trading. Investigations also revealed possession of **foreign government data, including confidential communications.** ### Detection & Response (Syndicate) - **How it was discovered:** Unknown, leading to arrests by the Singapore Police Force in September 2024. - **Response actions taken:** Arrests made; three individuals (Yan Peijian, Huang Qinzheng, Liu Yuqi) were convicted and sentenced to over two years in prison in November 2025. --- *(Note: The GDI flaw timeline relates to discovery by researchers and patching by Microsoft, not an active exploited incident provided in the text.)* ### GDI Vulnerability Disclosure Timeline - **Initial Access Vector (Exploitation):** Malformed enhanced metafile (EMF) and EMF+ records processed by `gdiplus.dll` or `gdi32full.dll`. - **Detection/Response:** Microsoft addressed CVE-2025-30388, CVE-2025-53766, and CVE-2025-47984 through **Patch Tuesday updates in May, July, and August 2025.** - **Context:** Researchers noted that one information disclosure vulnerability persisted for years due to an incomplete prior fix. ## Attack Methodology (Syndicate) | Technique | Method | | :--- | :--- | | **Initial Access** | Probing sites of interest for system vulnerabilities; Penetration attacks. | | **Persistence** | Use of RATs (Hundreds of different types) and likely the PlugX malware framework. | | **Privilege Escalation** | Not explicitly detailed, but necessary to access and exfiltrate PII databases. | | **Defense Evasion** | Use of established malware families (PlugX) and custom RATs to maintain stealth. | | **Credential Access** | Implied, necessary for database access, though specific methods (e.g., memory scraping) are not listed. | | **Discovery** | Probing sites for vulnerabilities. | | **Lateral Movement** | Use of RATs suggesting internal command and control structure establishment. | | **Collection** | Stealing databases of personally identifiable information (PII). | | **Exfiltration** | Transfer of stolen PII databases for trading purposes. | | **Impact** | Economic loss (through theft/cheating); Potential national security risk (possession of government data). | ## Impact Assessment (Syndicate) - **Financial:** Syndicate netted millions by cheating and trading stolen PII. - **Data Breach:** Theft of PII databases from overseas gambling companies. Potential compromise of foreign government communications. - **Operational:** Disruption to targeted gambling websites/companies. - **Reputational:** Negative exposure for the convicted individuals and the syndicate structure. ## Indicators of Compromise (Syndicate - Based on Malware Mentioned) - **Network Indicators:** C2 communications associated with PlugX infrastructure (Defanged example: C2\_IP\_ADDRESS). - **File Indicators:** PlugX binaries; Unknown malware files corresponding to the various RATs. - **Behavioral Indicators:** Unauthorized system enumeration, creation of persistent remote access channels, high-volume data transfer from database servers. ## Response Actions (Syndicate) - **Containment:** Singapore Police investigations and arrests (September 2024). - **Eradication:** Prosecution and sentencing of key operatives (November 2025). - **Recovery:** Not detailed, likely involved victims restoring databases and systems. ## Lessons Learned - **Persistent Threats:** Cybercrime syndicates operate long-term, involving complex structures (syndicate leader/tasked workers). - **Double Extortion/Impact:** The group leveraged cybercrime for financial gain while also potentially compromising sensitive state data, increasing the threat profile. - **Tool Diversity:** The use of commercialized malware (PlugX) alongside hundreds of custom RATs indicates a sophisticated, well-resourced adversary. - **GDI Fix Verification:** Patch failures are common; verifying the thoroughness of security patches, especially in core OS components like GDI, is critically challenging but necessary. ## Recommendations 1. **Threat Hunting:** Proactively hunt for known RAT infrastructures (like PlugX) within internal networks, especially in organizations dealing with high-value PII. 2. **Patch Management Rigor:** Implement secondary verification steps for patch efficacy, especially concerning fixes in core DLLs (`gdiplus.dll`, `gdi32full.dll`), to prevent lingering vulnerabilities. 3. **Data Classification:** Immediately classify and secure any systems housing foreign government data or sensitive communications if the organization interacts with international entities. 4. **Monitor OS Graphics Processing:** Implement EDR/XDR solutions capable of monitoring anomalous process behavior stemming from standard Windows API calls (like those related to EMF file rendering).

Hackers Weaponize Windows Hyper-V to Hide Linux VM and Evade EDR Detection
# Tool/Technique: Hyper-V Virtualization Exploitation (Curly COMrades Context) ## Overview The threat actor Curly COMrades is observed exploiting the native Windows Hyper-V virtualization platform to establish a hidden, persistent operating environment. By enabling the Hyper-V role on compromised Windows 10 hosts and deploying a minimalistic Alpine Linux virtual machine, the actor creates an execution sandbox isolated from traditional host-based EDR solutions, thus achieving evasion and persistence. ## Technical Details - Type: Technique (Leveraging legitimate virtualization platform) - Platform: Windows 10 (Host), Alpine Linux (Guest VM) - Capabilities: Evasion of host-based EDR, creating a hidden command execution environment, hosting custom malware (CurlyShell, CurlCat). - First Seen: The activity cluster has been active since late 2023, with Hyper-V weaponization observed in recent follow-up analysis (Post-August 2025). ## MITRE ATT&CK Mapping - **TA0005 - Defense Evasion** - T1542.003 - Pre-obfuscation: Use of Virtualization Technology - **TA0003 - Persistence** - T1547.001 - Registry Run Keys / Startup Folder (Indirectly, via establishing reliable VM access post-initial access) - **TA0011 - Command and Control** - T1071.001 - Application Layer Protocol: Web Protocols (via HTTP GET/POST) ## Functionality ### Core Capabilities * **Evasion:** Running malware (CurlyShell, CurlCat) inside a disposable, lightweight Linux VM isolates execution from the native Windows host monitoring tools (EDR). * **Lightweight Environment:** The deployed Alpine Linux VM has a highly reduced footprint (120MB disk space and 256MB memory). * **Reverse Shell:** Deployment of **CurlyShell**, an ELF binary that acts as a persistent reverse shell, connecting back to C2 servers. * **Data Flow:** Utilizes HTTP GET requests to poll for encrypted commands and HTTP POST requests to send back results. ### Advanced Features * **Custom Malware Families:** Utilizes **CurlyShell** (executes commands directly) and **CurlCat** (funnels traffic via SSH), both sharing a large code base optimized for execution within the VM. * **Reverse Proxy Capability:** Reliance on multiple proxy/tunneling tools (Resocks, Rsockstun, Ligolo-ng, CCProxy, Stunnel, SSH) to maintain flexible C2 resilience. * **Data Exfiltration/Transfer:** **CurlCat** is specifically noted for its role in bidirectional data transfer within the isolated environment. ## Indicators of Compromise * File Hashes: N/A (Specific hashes not provided in the text) * File Names: CurlyShell (ELF binary), CurlCat (Implied ELF binary or component) * Registry Keys: N/A * Network Indicators: Communication uses standard HTTP GET/POST, likely directed at C2 servers controlled by Curly COMrades (C2 addresses are not specified/defanged). Tunneling tools may generate outbound traffic associated with Resocks, Rsockstun, Ligolo-ng, or Stunnel. * Behavioral Indicators: Detection of Hyper-V role enablement on non-essential hosts. Deployment/execution of C++-compiled ELF binaries (CurlyShell) as headless background daemons on Windows hosts. ## Associated Threat Actors * Curly COMrades (Active since late 2023, targeting Georgia and Moldova, interests aligned with Russia). ## Detection Methods * Signature-based detection: Targeting known IOCs for associated tools (RuRat, Mimikatz, MucorAgent) used alongside the VM deployment. * Behavioral detection: Monitoring for unusual Hyper-V role enablement and subsequent creation of minimalistic Alpine Linux VMs. Monitoring for the execution of custom ELF binaries (CurlyShell) on a Windows infrastructure. * YARA rules: N/A (Specific rules not provided). ## Mitigation Strategies * **Prevention:** Disable or restrict the enablement of the Hyper-V role on endpoints unless explicitly required for business function. Implement strict controls over system configuration changes. * **Hardening:** Employ strong host-based security solutions (EDR/XDR) capable of monitoring virtualization layer activity and suspicious process execution, even for non-native binaries. Monitor for the execution of associated proxy/tunneling tools (Ligolo-ng, Stunnel). ## Related Tools/Techniques * **Custom Malware:** CurlyShell, CurlCat, MucorAgent (Modular .NET implant), RuRat. * **Third-Party Tools Used for Tunneling/Proxying:** Resocks, Rsockstun, Ligolo-ng, CCProxy, Stunnel. * **Other Implants Mentioned:** Mimikatz (Credential Harvesting). * **Technique Analogs:** Use of other virtual environments (VMware, KVM) for evasion.

ClickFix malware attacks evolve with multi-OS support, video tutorials
# Tool/Technique: ClickFix Attacks (Evolved Campaign) ## Overview ClickFix attacks are social-engineering driven campaigns where threat actors trick victims into pasting and executing malicious code or commands on their systems, often disguised as verification or software troubleshooting steps. Recent evolution introduces multimedia content (videos) and automated functions to increase pressure and reduce human error during execution. The typical goal is to deploy an information stealer payload. ## Technical Details - Type: Technique (Social Engineering combined with multi-stage execution payload delivery) - Platform: Multiple Operating Systems (Windows, macOS, Linux) - Capabilities: OS detection, automated command copying, video-guided infection process, time-based pressure. - First Seen: Not explicitly stated for the initial concept, but modern evolution noted in November 2025 research. ## MITRE ATT&CK Mapping - **TA0001 - Initial Access** - T1566 - Phishing - T1566.004 - Phishing: Phishing via Social Media (If delivered via compromised legitimate sites or SEO poisoning) - **TA0002 - Execution** - T1204 - User Execution - T1204.002 - User Execution: Malicious File - T1059 - Command and Scripting Interpreter - T1059.001 - Command and Scripting Interpreter: PowerShell - T1059.003 - Command and Scripting Interpreter: Windows Command Shell - **TA0005 - Defense Evasion** - T1216 - Signed Binary Proxy Execution (Implied by use of MSHTA/PowerShell) ## Functionality ### Core Capabilities - **Social Engineering:** Tricking users via fake CAPTCHA challenges (e.g., using a fake Cloudflare CAPTCHA disguise). - **Payload Delivery via Web:** Utilizing malicious JavaScript embedded on compromised websites or SEO-poisoned sites to execute the attack chain. - **Multi-OS Support:** Automatically detecting the victim's Operating System (Windows, macOS, Linux) to deliver tailored, correct commands for execution. ### Advanced Features - **Video Tutorials:** Embedding videos to guide victims step-by-step through the self-infection process, making the malicious sequence appear legitimate. - **Clipboard Automation:** Using JavaScript to automatically hide commands and copy them directly to the user's clipboard, minimizing manual entry and potential user mistakes. - **Pressure Tactics:** Implementing a one-minute countdown timer to rush the victim into executing commands without proper verification. - **Deception Counter:** Displaying a fake "users verified in the last hour" counter to simulate legitimacy. - **Living-off-the-Land (LotL) Payloads:** Delivering subsequent payloads utilizing native binaries like `MSHTA` on Windows and PowerShell scripts. ## Indicators of Compromise - File Hashes: Not provided in the context. - File Names: Not provided in the context, but payloads use system tools like `MSHTA` and PowerShell scripts. - Registry Keys: Not provided in the context. - Network Indicators: Initial infection vector utilizes malvertising on Google Search, leading to compromised websites or SEO-poisoned sites hosting the malicious JavaScript. Specific C2 domains are not detailed. - Behavioral Indicators: User interaction involving copying and pasting commands into a terminal/command prompt, often preceded by viewing a video tutorial under time pressure. Execution of native binaries like PowerShell or MSHTA in response to web interaction. ## Associated Threat Actors - Unspecified threat actors; the campaign is described as an evolving method utilized by attackers. ## Detection Methods - **Signature-based detection:** Potential for signatures targeting the specific JavaScript used for OS detection or clipboard manipulation. - **Behavioral detection:** Monitoring for user execution of terminal commands initiated immediately following web browsing sessions, especially if clipboard contents are piped directly into execution environments (powershell.exe, cmd.exe). Monitoring unusual execution of LotL binaries like MSHTA triggered by web content. - **YARA rules if available:** Not provided in the context. ## Mitigation Strategies - **Prevention:** Never execute commands pasted from untrusted web pages, especially when prompted by verification windows or CAPTCHAs. - **Hardening:** Implement robust Endpoint Detection and Response (EDR) solutions capable of detecting anomalous execution chains originating from web browsers or scripts. Restrict the use of high-privilege command-line tools like PowerShell for standard user operations where possible. - **User Education:** Train users to recognize urgency tactics (like timers) and suspicious requests to execute terminal commands as part of any online process. ## Related Tools/Techniques - PowerShell execution used in initial access. - Information Stealers (as the typical final payload). - Past ClickFix variants that relied exclusively on text instructions.
Mysterious 'SmudgedSerpent' Hackers Target U.S. Policy Experts Amid Iran–Israel Tensions
# Threat Actor: UNK_SmudgedSerpent This analysis is based on an intelligence report describing a previously unseen cyber activity cluster emerging between June and August 2025. ## Attribution & Identity * **Identification:** UNK_SmudgedSerpent (a never-before-seen threat activity cluster). * **Associations:** Shares tactical similarities with known Iranian cyber espionage groups, specifically: * TA455 (Smoke Sandstorm/UNC1549) * TA453 (Mint Sandstorm/Charming Kitten) * TA450 (MuddyWater/Mango Sandstorm) ## Activity Summary * **Recent Campaigns/Operations:** Conducted cyber attacks between June and August 2025, coinciding with heightened geopolitical tensions between Iran and Israel. * **Themes:** Leveraged lures related to domestic political instability in Iran and investigations into the militarization of the Islamic Revolutionary Guard Corps (IRGC). * **Engagement Tactics:** Engaged targets with benign conversations ("classic Charming Kitten attack") before attempting credential phishing. Involved attempts to verify the target's identity and email authenticity before proceeding with "collaboration." ## Tactics, Techniques & Procedures * **Initial Access:** Spearphishing (email). * **Lures:** Impersonated prominent U.S. foreign policy figures associated with think tanks (e.g., Brookings Institution, Washington Institute). Used domestic Iranian political lures. * **Credential Harvesting:** Directed victims to bogus landing pages to harvest Microsoft account credentials. In one instance, removed the password requirement after the target expressed suspicion, leading them to a spoofed OnlyOffice login page hosted on **thebesthomehealth[.]com**. * **Malware Deployment:** Delivered malicious link leading to an MSI installer disguised as Microsoft Teams. The MSI deployed legitimate Remote Monitoring and Management (RMM) software: * PDQ Connect. * **Post-Compromise:** Evidence suggests potential hands-on-keyboard activity to install a second RMM tool, **ISL Online**. * **Infrastructure Usage:** Used domains reminiscent of TA455 activity (health-themed domains, OnlyOffice references). ## Targeting * **Sectors:** Academics, Foreign Policy/Think Tanks. * **Geography:** Targeting U.S.-based experts. * **Victims:** Over 20 subject matter experts at a U.S.-based think tank focusing on Iran-related policy matters; a U.S.-based academic investigating the IRGC. ## Tools & Infrastructure * **Malware Families Used:** Legitimate RMM software used for malicious purposes: PDQ Connect, ISL Online. * **Infrastructure (C2, Domains, IPs):** * Credential harvesting hosted on: **thebesthomehealth[.]com** (used for spoofed OnlyOffice login). * Emails contained malicious URLs leading to an MSI installer. ## Implications This cluster appears to be an Iranian state-sponsored cyber espionage effort, given the geopolitical timing and tactical overlap with established Iranian APTs (TA455, TA453, TA450). The focus on foreign policy experts and think tanks suggests intelligence gathering related to U.S. policy toward Iran/Israel. The use of legitimate RMM software indicates an intent for persistent, difficult-to-detect remote access post-compromise. ## Mitigations * Heightened vigilance against spearphishing emails referencing recent geopolitical events or insider research topics related to Iran. * Scrutinize emails claiming to be from prominent policy figures or institutes (Brookings, Washington Institute). * Be wary of unexpected requests to click links to "join a meeting" or view documents, especially if they lead to external login pages for common productivity suites (Microsoft, OnlyOffice). * Organizations should monitor for the deployment of legitimate RMM tools (PDQ Connect, ISL Online) outside of approved software inventories. * Specific defense measures should incorporate TTPs noted from TA455 (monitoring for suspicious health/aerospace related domains used for C2 or hosting).

Google Uncovers PROMPTFLUX Malware That Uses Gemini AI to Rewrite Its Code Hourly
# Threat Actor: Unknown ## Attribution & Identity * **Identification:** An unknown threat actor discovered by Google Threat Intelligence Group (GTIG). * **Aliases/Associations:** None explicitly named in relation to PROMPTFLUX. The use of AI tools is noted in connection with a China-nexus actor separately, but this actor is not directly linked to PROMPTFLUX. ## Activity Summary * The actor is utilizing an experimental Visual Basic Script (VB Script) malware named PROMPTFLUX. * PROMPTFLUX incorporates a novel component dubbed the "Thinking Robot" which periodically queries the Gemini AI model API (Gemini 1.5 Flash or later) to dynamically rewrite and obfuscate its own source code to evade detection. * One observed variant rewrote its entire source code every hour using a prompt instructing the LLM to act as an "expert VB Script obfuscator." * The malware is assessed to be in a development or testing phase, currently lacking mechanisms to fully compromise a victim network or device. ## Tactics, Techniques & Procedures * **Self-Modification/Metamorphism:** Periodically queries an LLM (Gemini) via API to request new VBScript code specifically designed for obfuscation and antivirus evasion, resulting in "just-in-time" self-modification. * **Persistence:** Saves the newly obfuscated version to the Windows Startup folder. * **Lateral Movement/Propagation:** Attempts to copy itself to removable drives and mapped network shares. * **Logging:** Actively logs AI responses to `%TEMP%\thinking_robot_log.txt`. * **Obfuscation:** Specifically requests obfuscation techniques from the LLM to sidestep static signature-based detection. * **MITRE ATT&CK:** Not explicitly referenced in the provided text, but TTPs align conceptually with T1059.003 (Command and Scripting Interpreter: VisualBasic), T1055 (Process Injection - indirect), and T1588 (Obtain Capabilities - acquiring capability via AI augmentation). ## Targeting * **Sectors:** Broad, geography- and industry-agnostic approach, targeting a wide range of users. * **Geography:** Not specified. * **Victims:** Currently noted for testing/development; no specific compromised victims were mentioned. ## Tools & Infrastructure * **Malware Families Used:** PROMPTFLUX (written in VBScript). Other observed LLM-powered malware mentioned in passing include FRUITSHELL, PROMPTLOCK, PROMPTSTEAL (LAMEHUG), and QUIETVAULT. * **Infrastructure:** Utilizes the official Gemini AI model API, access is facilitated via a hard-coded API key. * **Defanged URLs/APIs:** Queries the Gemini API endpoint. ## Implications * Demonstrates an advanced adoption of Generative AI by threat actors, moving beyond productivity gains to create metamorphic malware capable of adjusting behavior during execution to counter security defenses. * The use of LLMs for automated, hourly code regeneration poses a significant challenge to static signature detection methods. ## Mitigations * Implement advanced behavioral monitoring and endpoint detection and response (EDR) to detect malicious script execution and activity patterns (e.g., unexpected API calls from scripts, self-modification). * Monitor network traffic for unusual outbound connections originating from user-level scripts to external commercial APIs (like the Gemini API). * Monitor user-level artifacts such as the `%TEMP%` directory for unusual log files generated by scripts (e.g., `thinking_robot_log.txt`). * Implement strict controls or monitoring around the Windows Startup folder entries created by non-standard processes.
Hackers Abuse OneDrive.exe via DLL Sideloading to Run Malicious Code
# Tool/Technique: Abuse of Microsoft OneDrive.exe via DLL Sideloading ## Overview This describes a sophisticated attack technique that exploits the legitimate Microsoft OneDrive application (`OneDrive.exe`) to execute arbitrary malicious code. The method relies on **DLL Sideloading**, tricking the Windows operating system into loading an attacker-controlled Dynamic Link Library (DLL) instead of a legitimate system or application library when `OneDrive.exe` starts. ## Technical Details - Type: Technique - Platform: Windows - Capabilities: Executes attacker code within the trusted process context of `OneDrive.exe`, bypassing traditional security measures reliant on application signatures; achieves persistence via DLL proxying and API hooking. - First Seen: Not explicitly stated, but the post implies a recent discovery by security researchers (referenced GitHub PoC exists). ## MITRE ATT&CK Mapping - **TA0004 - Privilege Escalation** - T1574 - Hijack Execution Flow - T1574.001 - DLL Side-Loading - **TA0005 - Defense Evasion** - T1218 - Signed Binary Proxy Execution (Indirectly, as the resulting process is signed) - **TA0002 - Execution** - T1055 - Process Injection (Related via API hooking/code execution flow) ## Functionality ### Core Capabilities - **DLL Sideloading:** Placing a malicious `version.dll` in the same directory as `OneDrive.exe` so that the Windows loader preferentially loads the malicious version when `OneDrive.exe` launches. - **Code Execution:** Runs arbitrary attacker code under the trusted process context of `OneDrive.exe`, inheriting its permissions (often elevated or with significant network access). - **Payload Execution:** After loading, the malicious code waits two seconds before executing the intended payload (e.g., launching `notepad` in the PoC, or potentially ransomware/backdoors in real attacks). ### Advanced Features - **DLL Proxying:** The malicious DLL exports the same functions as the legitimate library it replaces (`version.dll`). It forwards legitimate function calls to the real system library, ensuring the host application (`OneDrive.exe`) remains stable and continues to operate normally, thus hiding the malicious activity. - **API Hooking:** Utilizes **Vectored Exception Handling (VEH)** and memory page protection techniques to intercept Windows API calls (e.g., `CreateWindowExW`) at a low level and redirect execution flow to attacker-controlled code. - **Persistence/Re-arming:** The technique continuously re-arms itself during the application's runtime to maintain its active state. - **Delay Mechanism:** Introduces a two-second delay before payload execution to allow the initial, seemingly benign process launch to complete before the malicious activity begins. ## Indicators of Compromise - File Hashes: N/A (No specific hashes provided in the text) - File Names: `version.dll` (Malicious variant placed alongside `OneDrive.exe`) - Registry Keys: N/A - Network Indicators: N/A (The attacker may establish C2 connections post-execution, but none are specified.) - Behavioral Indicators: - Anomalous loading of `version.dll` by `OneDrive.exe`. - `OneDrive.exe` process exhibiting suspicious behavior (e.g., spawning command shells or deploying ransomware) after an initial quiescent period. - Detection of API hooking attempts related to core Windows functions originating from the `OneDrive.exe` process space. ## Associated Threat Actors - Not specifically named in the article. The details are based on a Proof-of-Concept discovered by security researchers (a GitHub link is referenced, suggesting independent discovery or initial publication). ## Detection Methods - **Signature-based detection:** Likely bypasses traditional file signature checks unless the specific malicious DLL hash is known. - **Behavioral detection:** Focus efforts on monitoring for advanced behaviors such as the use of VEH for API hooking, or unexpected process creation originating from a trusted Microsoft process like `OneDrive.exe`. Monitoring the initial loading dependencies of `OneDrive.exe` for unexpected DLLs is also key. - **YARA rules:** Not provided. ## Mitigation Strategies - **Prevention:** Implement strong application allow-listing policies. Restrict where executables and DLLs can be loaded from (e.g., enforcing execution only from Program Files directories). - **Hardening recommendations:** Employ application control solutions that monitor and restrict DLL loading behaviors, especially for system-level processes. Ensure OneDrive installations are protected from unauthorized write access to their installation directories. ## Related Tools/Techniques - **DLL Proxying:** A specific mechanism used in conjunction with DLL Sideloading to maintain host application functionality. - **Vectored Exception Handling (VEH) and API Hooking:** Used for advanced execution flow manipulation within the host process memory.
Operation SkyCloak Deploys Tor-Enabled OpenSSH Backdoor Targeting Defense Sectors
# Threat Actor: Unidentified (Associated with Operation SkyCloak) ## Attribution & Identity The threat actor remains unidentified, but the activity has been codenamed **Operation SkyCloak** by Seqrite Labs. Researchers assess with *medium confidence* that the attack shares tactical overlaps with prior activity attributed to **UAC-0125** (tracked by CERT-UA). The campaign is generally consistent with Eastern European-linked espionage activity. ## Activity Summary The actors are running a campaign named Operation SkyCloak, primarily distributed via phishing emails containing weaponized attachments (ZIP files hiding LNK files). The objective is to deploy a persistent backdoor leveraging OpenSSH and a custom Tor hidden service to maintain stealthy remote access. Archives related to the campaign were observed uploaded from Belarus to VirusTotal in October 2025. ## Tactics, Techniques & Procedures - **Initial Access:** Spearphishing via email using lures concerning military documents. - **Execution:** Opening a ZIP file containing a LNK file which triggers a multi-step infection chain starting with PowerShell commands. - **Defense Evasion (Anti-Analysis):** The PowerShell stager performs environmental checks: - Checks if the number of recent LNK files is $\ge 10$. - Checks if the current process count is $\ge 50$. If either condition fails, execution ceases, indicating a sandbox evasion technique. - **Persistence:** 1. Creation of a scheduled task named "githubdesktopMaintenance" set to run daily at 10:21 a.m. UTC upon user logon. This task executes a renamed `sshd.exe` (OpenSSH for Windows). 2. Creation of a second scheduled task to execute a customized Tor binary (`pinterest.exe`). - **Command and Control (C2):** Establishes a persistent backdoor that registers a Tor hidden service (`.onion` address). - **Data Exfiltration:** Exfiltrates system information and a unique system identifier (the `.onion` hostname) using a `curl` command after gaining access. - **Lateral Movement/Access:** Implements port forwarding for RDP, SSH, and SMB services to facilitate access through the Tor network. ## Targeting - **Sectors:** Defense sector. - **Geography:** Russia and Belarus. - **Victims:** Organizations within the defense sectors of Russia and Belarus. ## Tools & Infrastructure - **Malware Families Used:** Custom persistent backdoor utilizing OpenSSH (`sshd.exe` renamed), custom Tor binary (`pinterest.exe`), PowerShell stager. - **Infrastructure (C2):** A Tor hidden service employing **obfs4** for traffic obfuscation. A specific sample onion address observed was: `yuknkap4im65njr3tlprnpqwj4h7aal4hrn2tdieg75rpp6fx25hqbyd[.]onion`. - **File Paths:** Stores components in `%AppData%\Roaming\logicpro\`. ## Implications The operation indicates a highly sophisticated, state-sponsored or state-affiliated espionage effort targeting critical national security sectors in Eastern Europe. The use of OpenSSH combined with a Tor hidden service and obfs4 obfuscation suggests the actor prioritizes high-volume, resilient remote access while maintaining a significant degree of operational anonymity. ## Mitigations - **Email Security:** Enhance filtering for suspicious ZIP attachments, especially those containing LNK or nested compressed files. - **Endpoint Detection & Response (EDR):** Monitor for suspicious PowerShell execution, especially scripts attempting process/file counting for environmental checks. - **Network Monitoring:** Implement egress filtering and monitor for unexpected outbound traffic communicating with known Tor relay nodes or attempting to resolve `.onion` addresses. - **System Hardening:** Scrutinize scheduled tasks for suspicious names (`githubdesktopMaintenance`) running unknown executables, particularly renamed, legitimate binaries like `sshd.exe`. - **SSH/RDP Security:** Review authorized keys for OpenSSH deployments and restrict or monitor unusual attempts to use SFTP or SSH, especially if originating from unexpected local instances.
Malicious VSX Extension "SleepyDuck" Uses Ethereum to Keep Its Command Server Alive
# Tool/Technique: SleepyDuck (via juan-bianco.solidity-vlang extension) ## Overview SleepyDuck is a Remote Access Trojan (RAT) delivered via a malicious extension in the Open VSX registry (`juan-bianco.solidity-vlang`). Its primary purpose is to establish command and control over compromised developer workstations, gather system information, and maintain persistence through a resilient C2 mechanism leveraging the Ethereum blockchain. ## Technical Details - Type: Malware family (Remote Access Trojan) / Supply Chain Attack (Malicious Extension) - Platform: Developer workstations running code editors supporting Open VSX extensions (e.g., VS Code). - Capabilities: Remote access, system information exfiltration, resilient C2 updating/fallback via Ethereum contracts. - First Seen: Initial benign release on October 31, 2025; malicious update on November 1, 2025. ## MITRE ATT&CK Mapping - **TA0011 - Command and Control** - T1071 - Application Layer Protocol - *General C2 communication implied.* - **TA0009 - Collection** - T1082 - System Information Discovery - T1039 - Data from Local System - *Gathers system information (hostname, username, MAC address, timezone).* - **TA0005 - Persistence** - T1547.001 - Registry Run Keys / Startup Folder - *Triggered upon opening a new code editor window or selecting a `.sol` file, indicating execution based on application state.* - **TA0010 - Exfiltration** - T1041 - Exfiltration Over C2 Channel - *Exfiltrates gathered system information to the remote server.* ## Functionality ### Core Capabilities * **RAT Functionality:** Executes commands received from the remote server. * **Trigger Mechanism:** Executes upon opening a new code editor window or selecting a `.sol` file (Solidity source file). * **C2 Polling:** Checks for new commands every 30 seconds. * **Information Gathering:** Collects hostname, username, MAC address, and timezone. ### Advanced Features * **Resilient C2 Update via Ethereum:** Utilizes an Ethereum contract ([0xDAfb81732db454DA238e9cFC9A9Fe5fb8e34c465]) to store and update its C2 server address, making disruption difficult. * **C2 Fallback:** If the primary domain (`sleepyduck[.]xyz`) is seized, it queries RPC addresses to find the contract and extract the new server details. * **Emergency Command:** Capable of executing a universal emergency command to all compromised endpoints if necessary. * **Sandbox Evasion:** Includes techniques to detect and avoid execution within analysis environments. * **Initial C2:** Contacted `sleepyduck[.]xyz`. ## Indicators of Compromise - File Hashes: N/A (Information pertains to an extension installation) - File Names: `juan-bianco.solidity-vlang` (version 0.0.7 $\rightarrow$ 0.0.8) - Registry Keys: N/A - Network Indicators: - Initial C2 Domain: `sleepyduck[.]xyz` - Initial C2 Port (implied transaction): `:8080` (before jump to domain) - C2 Blockchain Contract Address: `0xDAfb81732db454DA238e9cFC9A9Fe5fb8e34c465` - Associated Actor Address (for context/tracking): `0x0edcfe26cf600fb56ae6aaf3f1d943c811314573` - Behavioral Indicators: Installation and execution triggered by VS Code/editor activity related to Solidity files; periodic network connections to update C2 information via Ethereum RPCs. ## Associated Threat Actors The source material does not explicitly name the threat actor group responsible for SleepyDuck, only referring to them as the "threat actor" who published the extension and managed the contract transactions. ## Detection Methods - Signature-based detection: Detection of the specific malicious extension name/ID in the Open VSX registry. - Behavioral detection: Monitoring for the extension hook execution upon opening `.sol` files, subsequent attempts to connect to external RPC providers, and C2 polling activity (e.g., connections to `sleepyduck[.]xyz`). - YARA rules: N/A (No file hashes provided, but rules could target the payload contained within the extension package). ## Mitigation Strategies * Exercise extreme caution when downloading third-party extensions, especially for specialized or less common repositories like Open VSX. * Prefer extensions from verified, trusted publishers on official marketplaces (like VS Code Marketplace, though it also requires vigilance). * Implement network monitoring to detect unusual external communication originating from development IDE processes (e.g., connections to known blockchain RPC nodes or suspicious domains). * Conduct supply chain hardening assessments for developer tools and associated marketplace extensions. ## Related Tools/Techniques * **Supply Chain Attacks targeting IDEs/Extensions:** Including other malicious extensions found on VS Code/Open VSX targeting Solidity developers, such as those previously disclosed by threat actors. * **Blockchain-based C2:** Use of decentralized infrastructure (like Ethereum smart contracts) to enhance C2 resilience, seen in various other malware families attempting to evade traditional domain takedowns. * **Related Batch Miner Payload:** The article mentions another set of extensions by "developmentinc" that deployed an immediate Monero mining payload using a batch script started via `cmd.exe` and configuring Defender exclusions, indicating a likely related threat actor profile utilizing opportunistic malware delivery.
Open VSX rotates access tokens used in supply-chain malware attack
# Incident Report: Open VSX Supply Chain Attack via Leaked Credentials ## Executive Summary The Open VSX registry experienced a supply-chain security incident after developers accidentally leaked access tokens in public repositories. Threat actors exploited these tokens to publish malicious extensions, attempting to distribute malware designed to steal developer credentials and cryptocurrency wallet data. The incident was contained after discovery, leading to immediate token revocation and the removal of malicious payloads, though the threat actors have since pivoted to targeting GitHub repositories using similar techniques. ## Incident Details - **Discovery Date:** Two weeks prior to the November 2, 2025 report (when Wiz researchers reported over 550 secret exposures). - **Incident Date:** Shortly after the token leak; malicious extensions published by threat actors a few days following the leak. - **Affected Organization:** Open VSX Registry (developed under the Eclipse Foundation). - **Sector:** Software Development / Open Source Ecosystem. - **Geography:** Not explicitly stated, assumed global due to the nature of the ecosystem. ## Timeline of Events ### Initial Access - **Date/Time:** Unknown, shortly before discovery (Wiz reported the leak two weeks prior to Nov 2, 2025). - **Vector:** Accidental exposure of access tokens/secrets in public source code repositories by developers. - **Details:** Leak involved over 550 secrets across Microsoft VSCode and Open VSX marketplaces. Some tokens allowed access to projects with up to 150,000 downloads. ### Lateral Movement - **Date/Time:** Following token compromise (A few days after the leak). - **Details:** Threat actors used compromised credentials to publish malicious extensions onto the Open VSX registry. The subsequent malware campaign, 'GlassWorm', attempted to steal developer credentials to extend the attacker's reach to other reachable projects. (Note: Open VSX disputed the 'self-spreading/replicating' nature of the malware). ### Data Exfiltration/Impact - **Date/Time:** During the malicious extension deployment period before removal. - **Details:** The primary impact was the deployment of malware (GlassWorm) attempting to steal developer credentials. The attacks specifically targeted cryptocurrency wallet data from 49 extensions, indicating financial motives. ### Detection & Response - **Date/Time:** Upon notification by Wiz researchers (leak discovery **two weeks prior**) and subsequent reporting by Koi Security on the active malware campaign. - **Response Actions:** - Open VSX and the Eclipse Foundation were notified. - As of October 21, all malicious extensions were removed from the Open VSX registry. - Associated access tokens were rotated or revoked. - The threat was confirmed as fully contained shortly after notification. ## Attack Methodology - **Initial Access:** Accidental leak of access tokens/secrets by developers into public source code repositories. - **Persistence:** Not detailed, as the immediate compromise was leveraging existing registry access via leaked tokens to publish malware. - **Privilege Escalation:** Not explicitly detailed; actors used existing high-privilege tokens to publish malicious extensions. - **Defense Evasion:** The GlassWorm malware utilized **invisible Unicode characters** (steganography) to hide malicious payloads within extensions. - **Credential Access:** The payload was designed to steal developer credentials. - **Discovery:** Not applicable in the traditional sense; actors leveraged pre-existing knowledge of the tokens/repositories. - **Lateral Movement:** Attempted by using stolen credentials to compromise other projects, though Open VSX stated it was not autonomous propagation. - **Data Exfiltration:** Targeted cryptocurrency wallet data from extensions. - **Impact:** Successful publication of malware to the registry, potential compromise of developer credentials, targeting financial data. ## Impact Assessment - **Financial:** Motivated by financial gain (targeting crypto wallet data). - **Data Breach:** Developer credentials were targeted. The actual number of affected users was believed to be overstated (35,800 downloads included bot traffic). - **Operational:** Temporary risk to the integrity of extensions hosted on Open VSX until remediation. - **Reputational:** Damage to trust in the Open VSX ecosystem as a secure alternative registry. ## Indicators of Compromise - **Network Indicators (Defanged):** None specified in the article. - **File Indicators:** Malicious VS Code extensions published carrying GlassWorm payloads hidden via Unicode steganography. - **Behavioral Indicators:** Uploading malicious extensions to the registry using legitimate, exposed access tokens; malware behavior focused on credential theft and targeting cryptocurrency data. ## Response Actions - **Containment:** Immediate removal of all malicious extensions from the Open VSX registry (completed by October 21). - **Eradication:** Rotation and revocation of all potentially compromised access tokens. - **Recovery:** Confirmation that the incident was fully contained with no ongoing impact. ## Lessons Learned - Accidental plaintext exposure of authentication secrets in public repositories remains a critical supply-chain vulnerability. - Attackers rapidly pivot to new tactics/platforms (e.g., moving from Open VSX to GitHub using the same Unicode steganography trick) upon exposure. - Download metrics can be inflated by threat actors, requiring careful assessment of actual user impact. ## Recommendations - Implement stringent secrets scanning (like the one performed by Wiz) immediately upon code commits. - **Shorten token lifetimes** significantly to minimize the impact window of any future leaks. - Introduce **faster credential revocation workflows** for compromised secrets. - Implement **automated security scanning for extensions** during the publication process. - Collaborate with other marketplaces (like Microsoft VS Marketplace) to share threat intelligence regarding discovered vulnerabilities and attacker TTPs.
LABScon25 Replay | LLM-Enabled Malware In the Wild
# Tool/Technique: LLM-Enabled Malware (General Threat Concept) ## Overview LLM-Enabled Malware refers to malicious payloads that integrate Large Language Model (LLM) capabilities directly into their operation. The key characteristic distinguishing these threats is their ability to generate malicious code or content dynamically at runtime, bypassing traditional static analysis methods that rely on pre-embedded or fixed malicious artifacts. ## Technical Details - Type: Technique / Malware Category - Platform: Not explicitly stated, but likely Windows/x64 initially (typical for ransomware/APT tools), capable of impacting any system where LLM APIs are accessed. - Capabilities: Runtime code generation, adaptive behavior, weaponization of LLM functions. - First Seen: Research presented in November 2025, indicating emerging in-the-wild activity prior to this date. ## MITRE ATT&CK Mapping This emerging concept spans multiple tactics, focused heavily on evading detection and executing code: - **TA0002 - Execution** - T1059.005 - Command and Scripting Interpreter: Visual Basic - T1620 - Instruction Injection (Potential for dynamically generated code execution) - **TA0005 - Defense Evasion** - T1140 - Deobfuscate/Decode Files or Information (If prompts/keys are decoded) - T1027 - Obfuscated Files or Information (Runtime generation acts as a form of obfuscation) ## Functionality ### Core Capabilities - Leveraging embedded Large Language Model capabilities within the malicious payload. - Generating malicious code or content dynamically at runtime, rather than relying on static embedding. - Hardcoding configuration artifacts (API keys, prompts) which serves as a critical detection opportunity. ### Advanced Features - Potential for highly adaptive or context-aware malicious operations due to LLM integration. - Discovery of novel samples like "MalTerminal," potentially the earliest known LLM-enabled malware. ## Indicators of Compromise Indicators focus on the hardcoded dependencies used by the malware creators: - **File Hashes:** Over 7,000 samples and 6,000+ unique API keys identified in a retrohunt, no specific hashes provided in the summary. - **File Names:** Not detailed, but includes examples like "MalTerminal". - **Registry Keys:** Not detailed. - **Network Indicators:** Reliance on external LLM API endpoints (e.g., OpenAI infrastructure) for generating payloads or performing tasks. (No specific defanged URLs provided). - **Behavioral Indicators:** Executing processes that interact with API key identifiers or structures associated with major LLM providers. ## Associated Threat Actors - **APT28:** Associated with campaigns like LameHug/PROMPTSTEAL. - General Adversaries leveraging AI themes or tools. ## Detection Methods The research highlights limitations with traditional methods and proposes novel hunting techniques: - **Signature-based detection:** Ineffective against runtime-generated code. - **Behavioral detection:** Needs enhancement to detect dynamic execution linked to LLM calls. - **YARA Rules:** Used for *wide API key detection*, targeting specific provider key structures (e.g., OpenAI's Base64-encoded identifiers). - **Prompt Hunting:** Searching for hardcoded prompt structures within binaries, often paired with lightweight LLM classifiers to verify malicious intent. ## Mitigation Strategies - Focus detection efforts on the static artifacts that cannot be obfuscated: hardcoded API keys and prompts. - Implement comprehensive YARA rules targeting known LLM API key formats embedded in binaries. - Develop and apply lightweight LLM classifiers trained to identify malicious intent within dynamically generated code segments. ## Related Tools/Techniques - **PromptLock ransomware:** An example of malware leveraging LLM capabilities. - **LameHug/PROMPTSTEAL:** Specific campaigns attributed to APT28 utilizing LLM components. - **MalTerminal:** Potentially the earliest discovered LLM-enabled malware.
North Korean Hackers Lure Defense Engineers With Fake Jobs to Steal Drone Secrets
# Threat Actor: Lazarus Group (and associated clusters) ## Attribution & Identity * **Attribution:** Threat actors with ties to North Korea. * **Known Aliases and Associated Groups:** Lazarus Group, APT-Q-1, Black Artemis, Diamond Sleet (formerly Zinc), Hidden Cobra, TEMP.Hermit, UNC2970. * **Associated Clusters/Campaigns:** DeathNote, NukeSped, Operation In(ter)ception, Operation North Star. ## Activity Summary The actors are currently engaged in a long-running cyber espionage campaign known as **Operation Dream Job**, first exposed in 2020. The latest observed activity wave began in late March 2025, targeting European defense industry companies, specifically those involved in the Unmanned Aerial Vehicle (UAV) sector, aligning with North Korea's drone program scaling efforts. Historically, the actor has been operational since at least 2009 and previously targeted entities in India and Poland (early 2023). The primary objective of Operation Dream Job is to steal proprietary information and manufacturing know-how. ## Tactics, Techniques & Procedures * **Social Engineering:** Leveraging spearphishing lures involving "lucrative but faux job offers" (akin to Contagious Interview). Targets are approached with fake job opportunities to gain initial access. * **Initial Compromise:** Targets receive a decoy document containing a job description and a trojanized PDF reader file to open it. * **Execution Chain:** The attack chain leads to binary execution, which is responsible for sideloading a malicious DLL. * **Payload Deployment:** The DLL drops the main payload, **ScoringMathTea**, and a sophisticated downloader, **BinMergeLoader**. * **Secondary Payload Fetching:** BinMergeLoader utilizes Microsoft Graph API and tokens to fetch additional payloads. * **Polymorphism:** The group consistently deploys ScoringMathTea using similar methods to trojanize open-source applications, employing polymorphism to evade detection. ## Targeting * **Sectors:** Defense Industry, Aerospace, Drone/UAV Sector, Metal Engineering, Aircraft Component Manufacturing. * **Geography:** Europe (Southeastern Europe, Central Europe). * **Victims:** Specific entities mentioned include a metal engineering company in Southeastern Europe, a manufacturer of aircraft components in Central Europe, and a defense company in Central Europe. ## Tools & Infrastructure * **Malware families used:** * **ScoringMathTea:** Advanced Remote Access Trojan (RAT) supporting approximately 40 commands to achieve full control. (Also known as ForestTiger). * **MISTPEN:** Used in connection with this campaign, though BinMergeLoader functions similarly. * **BinMergeLoader:** Sophisticated downloader used to fetch additional payloads. * **Infrastructure:** Specific IPs/URLs were not detailed in the summary, though the use of Microsoft Graph API for payload fetching is noted. ## Implications This activity signifies a strategic focus by North Korea on acquiring sensitive technology related to drone development from European defense contractors. The consistent use of high-touch social engineering (fake job offers) combined with established, polymorphic malware like ScoringMathTea suggests a well-resourced and patient cyber espionage apparatus dedicated to military-technological gain. ## Mitigations * Implement strict verification processes for unexpected job offers or unsolicited communications, especially those leading to file execution. * Enhance endpoint detection and response capabilities to monitor for DLL sideloading techniques. * Review configurations related to Microsoft Graph API usage and token authentication for anomalous activity indicative of third-party payload retrieval. * Train personnel, particularly engineering and R&D staff, on social engineering tactics focused on career opportunities.
Mapping latest Lumma infrastructure
# Threat Actor: Lumma Stealer Operators ## Attribution & Identity The threat actor group responsible for deploying the Lumma malware is referred to as **Lumma**. The summary focuses on the infrastructure used by the operators of this malware. No specific nation-state or cybercriminal syndicate attribution is provided in the text, only the identification of the malware operator based on infrastructure analysis. ## Activity Summary The article details the ongoing hunt and mapping of the current Command and Control (C2) and distribution infrastructure associated with the Lumma information stealer. Despite law enforcement efforts, the operators are actively generating new malware distribution points and C2 domains, exhibiting high resilience. The analysis centered around pivoting from an initial C2 domain (`nonsazv[.]qpon`) to map related infrastructure clusters. ## Tactics, Techniques & Procedures - **Infrastructure Reuse/Clustering:** Operators rely heavily on concentrated hosting infrastructure for deploying resources, making clustering possible even with domain rotation. - **Domain Generation:** Threat actors frequently generate multiple domains using similar naming conventions (e.g., variations incorporating `.qpon`). - **Delivery Mechanism:** The infection chain starts with a malicious `.zip` file containing the Lumma malware, which subsequently communicates with C2 servers. - **Pivoting Techniques:** The analysis utilized URLScan searches based on domain naming conventions (`*.qpon`) and ASN registration to discover related domains. Certificate fingerprint hashing (Used via Validin) served as a critical pivot point to uncover related hosts and domains associated with Lumma communications. ## Targeting - **Sectors:** Not explicitly detailed, though Lumma is typically an information stealer targeting credentials, cryptocurrency wallets, and sensitive files. - **Geography:** Not specified in the context of victims, but the infrastructure is hosted across various international providers (US-based, European ASNs). - **Victims:** No specific victim organizations are named, but the activity implicitly targets individuals or organizations deploying systems vulnerable to credential theft via Lumma. ## Tools & Infrastructure - **Malware Families Used:** Lumma (Information Stealer) - **Infrastructure (C2, domains, IPs):** - Initial Pivot Domain: `nonsazv[.]qpon`, `pictuqyr[.]qpon`, `pattemqr[.]qpon`, `apothfya[.]qpon`, `fruiunp[.]qpon`, `brunsmmv[.]qpon`, `bac-bank[.]qpon` - Associated TLDs: `.top`, `.xyz`, `.qpon`, `.ru` - **ASN Clusters Identified:** - ASN 210644 (Aeza) - Known bulletproof hosting provider. - ASN 8254 (ROUTE95 GREEN FLOID LLC) - Hosting many Lumma-flagged domains. - ASN 48753 (Ava Host Srl) - Routerhosting - Proton66 - **IP Addresses:** - `46.28.71.142` (Route95, ASN8254) - `217.156.66.212` (Ava Host Srl, ASN48753) - `172.86.89.51` (Used for certificate fingerprint pivoting) ## Implications Lumma operators demonstrate operational persistence and effective infrastructure management, relying on rotating domains while maintaining continuity by recycling specific, resilient hosting providers (bulletproof/favorable ASNs like Aeza, Route95, Proton66, Routerhosting). This concentration of infrastructure provides high detection opportunities via ASN and TLS fingerprint monitoring, despite successful domain camouflage. ## Mitigations - Focus detection efforts beyond individual domain names by clustering malicious infrastructure based on shared hosting providers (ASNs like Aeza, Route95, Proton66, Routerhosting). - Implement monitoring for TLS certificate fingerprints associated with known Lumma C2 infrastructure to quickly identify newly deployed domains on the same hosts. - Enhance network defenses to immediately block communications originating from the identified bulletproof hosting providers used by the actor. - Ensure endpoint security detects the initial infection vector, specifically the malicious `.zip` file deployment chain.

Chinese hackers scanning, exploiting Cisco ASA firewalls used by governments worldwide
# Threat Actor: Storm-1849 (Also referred to as UAT4356) ## Attribution & Identity * **Attribution:** China-based threat group. * **Known Aliases:** UAT4356. * **Associated Groups:** Implied connection to state-sponsored activity, given the targeting profile and comparison to the ArcaneDoor campaign, which CISA linked to nation-state hackers. ## Activity Summary Storm-1849 is actively engaged in scanning and exploiting vulnerabilities in Cisco Adaptive Security Appliances (ASA) devices. The targeting, first noted by Cisco in 2024, has continued throughout October (of the reporting year), with researchers tracking persistent attempts to compromise these firewalls. Activity saw a brief lull between October 1st and October 8th, likely corresponding with China’s Golden Week holiday. The group has shown persistence despite the issuance of CISA emergency directives to patch critical vulnerabilities. ## Tactics, Techniques & Procedures - **Exploitation Chain:** Hackers were observed chaining together vulnerabilities CVE-2025-30333 and CVE-2025-30362. - **Persistence Mechanisms:** Sophisticated methods were used to maintain access to exploited ASAs such that the compromise persisted through device reboots and system upgrades. - **Initial Access:** Scanning and exploitation targeting vulnerable government edge devices (Cisco ASA). ## Targeting * **Sectors:** Government, defense industry, and financial institutions. * **Geography:** Worldwide targeting of federal, state, and local government IP addresses, including the U.S., India, Nigeria, Japan, Norway, France, the U.K., the Netherlands, Spain, Australia, Poland, Austria, UAE, Azerbaijan, and Bhutan. * **Victims:** Specific targets tracked include U.S. federal agencies (12 IP addresses), U.S. local and state government entities (11 IP addresses), U.S. financial institutions, and defense contractors. ## Tools & Infrastructure * **Malware Families Used:** Not explicitly named in the provided text, but the activity leverages the exploitation of Cisco ASA software. * **Infrastructure (C2, domains, IPs):** Exploitation activity targeted 35 specific IP addresses associated with government entities across multiple countries. (Specific IPs and domains are not listed/defanged in the source text). ## Implications Storm-1849 is a rapidly emerging and globally active threat actor specializing in exploiting widely deployed, critical infrastructure devices (Cisco ASA). Their continued activity against government entities post-emergency directive suggests high operational tempo and a focus on gaining persistent access to government networks globally, positioning them as a significant player alongside established groups like Volt Typhoon. ## Mitigations - Immediately patch Cisco ASA devices for vulnerabilities CVE-2025-30333 and CVE-2025-30362, as exploitation is occurring with "alarming ease." - Implement mitigation strategies to ensure persistence mechanisms (gained through exploitation) are removed, paying close attention to ensuring access does not survive reboots or system upgrades. - Monitor network perimeter devices (ASAs) for signs of unauthorized persistence mechanisms.

Nation-State Hackers Deploy New Airstalk Malware in Suspected Supply Chain Attack
# Threat Actor: CL-STA-1009 ## Attribution & Identity **Identification:** Suspected nation-state threat actor. **Known Aliases and Associated Groups:** Tracked by Palo Alto Networks Unit 42 under the moniker **CL-STA-1009** ("CL" for cluster, "STA" for state-backed motivation). ## Activity Summary The threat actor is linked to the distribution of a new malware family named **Airstalk** as part of a suspected supply chain attack. The purpose of the activity appears to be covert surveillance and data exfiltration from compromised systems. ## Tactics, Techniques & Procedures - **Supply Chain Compromise:** The campaign likely involves injecting the malware via a supply chain vector. - **API Misuse for C2:** Abusing the legitimate **AirWatch API** (now Workspace ONE Unified Endpoint Management) to establish a covert Command and Control (C2) channel. - **Dead Drop Resolver:** Using the API's custom attributes feature to store necessary interaction information (dead drop). - **Multi-threaded C2:** Employs a multi-threaded C2 communication protocol. - **Code Variant Development:** Operates at least two variants: PowerShell and a more capable .NET version. - **Code Signing:** .NET samples have been observed signed with a "likely stolen" certificate from **Aoteng Industrial Automation (Langfang) Co., Ltd.** - **Persistence (PowerShell Variant):** Uses a scheduled task for persistence. - **Masquerading (.NET Variant):** The .NET variant attempts to mimic an AirWatch Helper utility (`AirwatchHelper.exe`). - **C2 Communication Structure:** Uses specific messages for C2: "CONNECT" (initiation), "CONNECTED" (response), "ACTIONS" (tasks), and "RESULT" (output transmission). File exfiltration uses the API's "blobs" feature. ## Targeting **Sectors:** Not explicitly detailed, but the reliance on Mobile Device Management (MDM) APIs suggests targeting organizations managing extensive fleets of endpoints, likely including enterprise and government entities. **Geography:** Not specified in the provided context. **Victims:** No specific victims are named in the context provided. ## Tools & Infrastructure - **Malware Families Used:** Airstalk (PowerShell and .NET variants). - **Infrastructure:** Leverages the **AirWatch/Workspace ONE MDM API** for C2. - **PowerShell C2 Endpoint:** Uses the `[/api/mdm/devices/](http://kb.omnissa.com/s/article/50117934)` endpoint. - **Authentication/Authorization:** Likely leveraging a stolen certificate for artifact signing. ## Implications The use of legitimate MDM APIs for C2 significantly raises the profile of this threat. It allows the malware to blend into legitimate enterprise traffic, making detection based on network signatures difficult. The introduction of a more advanced .NET version indicates active research and refinement of the malware by the actor. Targeting MDM infrastructure indicates a high-value, persistent intent, potentially for widespread device compromise. ## Mitigations - **Certificate Monitoring:** Monitor for authentic code signed by Aoteng Industrial Automation (Langfang) Co., Ltd. in unexpected contexts. - **MDM API Visibility:** Implement enhanced logging and anomaly detection on AirWatch/Workspace ONE API usage, specifically monitoring unexpected traffic patterns on the `/api/mdm/devices/` endpoint or unusual custom attribute modifications/data submissions. - **Application Control:** Restrict execution of unsigned or newly compiled PowerShell and .NET binaries in enterprise environments. - **Endpoint Defense:** Deploy advanced EDR solutions capable of detecting persistence mechanisms like unauthorized scheduled tasks and in-memory theft operations. - **Browser Security:** Implement protections targeting browser artifact theft (cookies, history) across Chrome, Microsoft Edge, and Island browser.
You've reached the end of the gallery.